Setting Up Cisco Anyconnect
In my previous post I gave you some recommendations on why use a VPN. Today I want to explain you how to configure remote access it using a Cisco Firepower Threat Defense (FTD) firewall managed by Firepower Management Center (FMC).
- Setting Up Cisco Anyconnect Vpn Server
- Cisco Anyconnect Vpn Client Download
- Cisco Anyconnect Download Windows 10
- Setting Up Cisco Anyconnect
How to configure Remote Access VPN step by step:
Note: You must be approved by WKU ITS Security in order to use the Cisco VPN. If you have not requested access yet, please follow these instructions. Note: This process will involve the computer you need to use the Cisco AnyConnect VPN on and your cell phone.Please have both ready before you start this process. Go here from the computer that you will use the Cisco VPN on. Launch the Cisco AnyConnect Secure Mobility Client client. If you don't see Cisco AnyConnect Secure Mobility Client in the list of programs, navigate to Cisco Cisco AnyConnect Secure Mobility Client. When prompted for a VPN, enter su-vpn.stanford.edu and then click Connect. Enter the following information and then click OK.
When autocomplete results are available use up and down arrows to review and enter to select. AnyConnect Secure Mobility Client v4.x Login. Such as setting your. / How To Configure AnyConnect SSL VPN on Cisco ASA 5500 Virtual private networks, and really VPN services of many types, are similar in function but different in setup. At the end of this post I also briefly explain the general functionality of a new remote access vpn technology, the AnyConnect SSL client VPN.
Now we will see how to configure a FTD device, to allow AnyConnect connections and to use an internal Microsoft NPS server for authenticating the users.
- Windows 10 client
- Cisco virtual FTD running version 6.6.0
- Cisco FMC running version 6.6.0
FMC configurations:
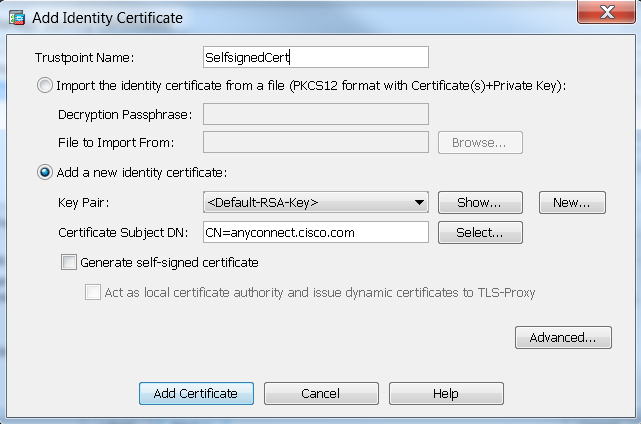
Create a new certificate for FTD
On the tab that will be showed please select the FTD where you want to add the certificate and who is enrolling that certificate.
In our guide we are using FMC as internal CA, that it’s a self signed certificate. We are not using a corporate CA or an external CA.
Add radius server on FMC
Add pool of addresses for VPN client
Uploading AnyConnect Images

Setting Up Cisco Anyconnect Vpn Server
On the next menu you need to select the interface where you have to enable the SSL VPN access and which certificate you need to use for establishing VPN tunnel.
If you enable “Bypass Access Control policy for decrypted traffic” you are not able to perform any kind of filter on Access Policy from incoming VPN traffic.
Cisco Anyconnect Vpn Client Download
Configure no NAT policy
The last step needed on FMC is to configure a new NAT policy to avoid that the traffic from the LAN to the VPN client will be natted.
Now you are able to deploy the configuration to you FTD!
We need to perform last steps on Windows NPS before to say that we have finished to configure a remote access VPN on Cisco FTD
Windows NPS configuration
Device management allows you to easily edit and add new devices.
Contents
Cisco Anyconnect Download Windows 10
Accessing Device Management
Setting Up Cisco Anyconnect
If your administrator enabled self-service device management, the Duo Prompt displays a 'My Settings & Devices' link on the left.
If you enabled the option to automatically send you an authentication request via push or phone call, you'll need to cancel the push or phone call in progress before you can click the 'My Settings & Devices' link.
To manage your devices, choose an authentication method and complete two-factor authentication (you may need to scroll down to see all authentication options). You can't get in to the device management portal if you do not have access to any enrolled devices; you'll need to contact your Duo administrator for help.
After authenticating you'll see the device management portal. This is where you can enroll a new device by clicking Add another device and following the device enrollment steps, or reactivate, edit, or delete your existing devices.
To exit My Settings & Devices, click the Done button below your listed devices or click your organization's logo on the left (or the Duo logo if shown).
Default Authentication Options
If you authenticate with more than one device, you can specify which you would like to be the default. Click the Default Device: drop-down menu and pick your default device for authentication. Click Save if you're done making changes.
If this is the device you'll use most often with Duo then you may want to enable automatic push requests by changing the When I log in: option and changing the setting from 'Ask me to choose an authentication method' to 'Automatically send this device a Duo Push' or 'Automatically call this device' and click Save. With one of the automatic options enabled Duo automatically sends an authentication request via push notification to the Duo Mobile app on your smartphone or a phone call to your device (depending on your selection).
Manage Existing Devices
Click the Device Options button next to any of your enrolled devices to view the actions available for that type of device. You can Reactivate Duo Mobile for an enrolled smartphone, Change Device Name for any type of phone, or delete any authentication device.
Reactivate Duo Mobile
Click the Reactivate Duo Mobile button if you need to get Duo Push working on your phone, for example, if you replaced your phone with a new model but kept the same phone number. After answering some questions about your device, you'll receive a new QR code to scan with your phone, which will complete the Duo Mobile activation process.
Change Device Name
Clicking Change Device Name will open up an interface to change the display name of your phone (hardware tokens can't be renamed). Type in the new name and click Save.
After successfully modifying your phone's name, not only will you see this from now on when managing devices, but it will also be how your phone is identified in the authentication dropdown.
Remove Device
Click the trash can button to delete a phone or token device.
Note: You may not remove your last device. If you wish to remove it, first add another, then delete the original. If you are unable to delete a device, contact your administrator to have it removed.
You are given the chance to confirm or cancel deleting the authentication device.
The device is deleted. It can no longer be used to approve Duo authentication requests.
Add a New Device
To add a new authentication device, click the Add a new device link on the left side of the Duo Prompt. You'll be taken to the new device enrollment prompt.
See the instructions for adding a new device.
